Threat intel platforms Courses
Explore instructor-led and hybrid programs aligned to practical Threat intel platforms use cases across industries.
Available Threat intel platforms Courses
Showing 1-4 of 4 courses
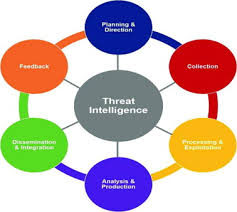
Digital Forensics
Training Course on Advanced Threat Actor Profiling and Attribution equips security professionals with the cutting-edge skills and actionable intelligence needed to proactively identify, track, and disrupt malicious activities, transforming reactive incident response into proactive threat hunting and strategic risk mitigation.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Advanced Threat Actor Profiling and Attribution equips security professionals with the cutting-edge skills and actionable intelligence needed to proactively identify, track, and disrupt malicious activities, transforming reactive incident response into proactive threat hunting and strategic risk mitigation.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore

Digital Forensics
Training Course on Analyzing Advanced Persistent Threat (APT) Malware is designed to equip cybersecurity professionals with advanced skills to detect, analyze, and mitigate APT malware using cutting-edge threat intelligence tools and reverse engineering techniques.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Analyzing Advanced Persistent Threat (APT) Malware is designed to equip cybersecurity professionals with advanced skills to detect, analyze, and mitigate APT malware using cutting-edge threat intelligence tools and reverse engineering techniques.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Digital Forensics
Training Course on Cyber Threat Intelligence for Proactive Defense delves into the foundational principles and advanced practices of CTI, equipping participants with the knowledge and skills to build robust threat intelligence programs. From data collection and analysis to threat hunting and strategic intelligence dissemination, the course covers the entire CTI lifecycle.
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Cyber Threat Intelligence for Proactive Defense delves into the foundational principles and advanced practices of CTI, equipping participants with the knowledge and skills to build robust threat intelligence programs. From data collection and analysis to threat hunting and strategic intelligence dissemination, the course covers the entire CTI lifecycle.
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Digital Forensics
Training Course on Malware Campaign Tracking and Attribution equips participants with tactical knowledge and practical techniques for malware reverse engineering, infrastructure pivoting, behavioral analytics, threat actor profiling, and intelligence enrichment for attribution.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Malware Campaign Tracking and Attribution equips participants with tactical knowledge and practical techniques for malware reverse engineering, infrastructure pivoting, behavioral analytics, threat actor profiling, and intelligence enrichment for attribution.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore