Training Course on Incident Response Reporting for Compliance and Stakeholders
Training Course on Incident Response Reporting for Compliance and Stakeholders is designed to equip professionals with the essential skills and knowledge to navigate the complexities of incident response reporting, ensuring compliance with legal and regulatory requirements while maintaining stakeholder trust.
Skills Covered
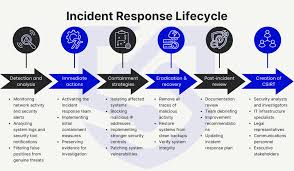
Course Overview
Training Course on Incident Response Reporting for Compliance and Stakeholders
Introduction
In an era of escalating cyber threats and stringent regulatory landscapes, the ability to effectively respond to and report on security incidents is no longer just an IT function but a critical business imperative. Training Course on Incident Response Reporting for Compliance and Stakeholders is designed to equip professionals with the essential skills and knowledge to navigate the complexities of incident response reporting, ensuring compliance with legal and regulatory requirements while maintaining stakeholder trust. Participants will delve into the critical components of a robust incident response framework, from initial detection and analysis to post-incident review and communication. We will explore how to translate technical incident data into clear, concise, and actionable reports for a variety of audiences, including executive leadership, legal counsel, regulatory bodies, and customers.
This course moves beyond the technical aspects of incident response to focus on the strategic communication and compliance challenges that organizations face in the aftermath of a security breach. We will examine the nuances of stakeholder engagement, emphasizing the importance of timely, transparent, and targeted communication to mitigate reputational damage and financial loss. Through a combination of expert instruction, real-world case studies, and practical exercises, attendees will learn how to develop and implement an incident response reporting strategy that not only meets compliance obligations but also strengthens the organization's overall cybersecurity posture and resilience.
Course Duration
10 days
Course Objectives
Upon successful completion of this course, participants will be able to:
- Develop a comprehensive incident response reporting framework aligned with business objectives and regulatory mandates.
- Master the art of stakeholder analysis and communication to effectively manage expectations during and after a security incident.
- Craft clear, concise, and impactful incident reports for diverse audiences, including C-suite executives, legal teams, and technical staff.
- Ensure compliance with key regulations and standards such as GDPR, HIPAA, PCI DSS, and NIST.
- Leverage threat intelligence and incident data to provide actionable insights and recommendations for future prevention.
- Effectively manage media and public relations during a crisis to protect the organization's reputation.
- Understand the legal and ethical considerations surrounding incident disclosure and data breach notifications.
- Implement a continuous improvement process for incident response reporting based on lessons learned from past events.
- Utilize industry-standard tools and technologies for incident documentation and reporting.
- Confidently lead and participate in post-incident review meetings to drive meaningful change.
- Integrate incident response reporting into the organization's overall risk management program.
- Prepare for and respond to audits and regulatory inquiries related to security incidents.
- Foster a culture of security awareness and accountability across the organization.
Organizational Benefits
Organizations that invest in this training will realize significant benefits, including:
- Enhanced Compliance: Ensure adherence to a complex web of international and industry-specific regulations, avoiding costly fines and penalties.
- Reduced Reputational Damage: Proactively manage stakeholder communications to maintain trust and confidence in the brand.
- Improved Decision-Making: Equip leadership with the timely and relevant information needed to make strategic decisions during a crisis.
- Increased Operational Resilience: Minimize business disruption and expedite recovery from security incidents.
- Strengthened Security Posture: Identify and address systemic weaknesses in security controls through effective post-incident analysis.
- Lowered Financial Impact: Mitigate the financial consequences of security incidents through efficient response and reporting.
Target Participants
This course is ideal for a wide range of professionals, including:
- Incident Response Team Members
- IT and Security Managers
- Compliance and Privacy Officers
- Legal and Corporate Counsel
- Public Relations and Communications Specialists
- Risk Management Professionals
- Executive Leadership (CEOs, CIOs, CISOs)
- Internal and External Auditors
Course Modules
Module 1: The Foundations of Incident Response Reporting
- The Evolving Threat Landscape and the Need for Effective Reporting
- Key Components of an Incident Response Framework (NIST, ISO 27001)
- The Intersection of Incident Response, Compliance, and Stakeholder Management
- Defining Roles and Responsibilities in Incident Reporting
- Case Study: Analysis of a major data breach and its reporting lifecycle.
Module 2: Legal and Regulatory Compliance Deep Dive
- Navigating the Global Regulatory Maze: GDPR, CCPA, and Beyond
- Industry-Specific Requirements: HIPAA for Healthcare, PCI DSS for Finance
- Understanding Contractual and Legal Obligations for Reporting
- The Role of Cyber Insurance in Incident Response and Reporting
- Case Study: A comparative analysis of breach notification laws in different jurisdictions.
Module 3: Stakeholder Analysis and Communication Strategy
- Identifying and Prioritizing Key Stakeholders
- Developing a Proactive Stakeholder Communication Plan
- Tailoring Messages for Different Audiences (Internal and External)
- Managing Expectations and Building Trust During a Crisis
- Case Study: Deconstructing the communication strategy of a company during a public security incident.
Module 4: Crafting Compelling Incident Reports for Executive Leadership
- Translating Technical Jargon into Business-Friendly Language
- Focusing on Business Impact, Risk, and Remediation
- Presenting Actionable Recommendations for Strategic Decision-Making
- Visualizing Data for Maximum Impact
- Case Study: Review and critique of sample executive-level incident reports.
Module 5: Technical and Forensic Reporting for IT and Security Teams
- Documenting the Incident Timeline and Key Findings
- Detailing the Attack Vector, Scope, and Impact on Systems
- Outlining Containment, Eradication, and Recovery Efforts
- Preserving the Chain of Custody for Evidence
- Case Study: Writing a detailed technical report for a complex malware incident.
Module 6: Reporting to Regulatory Bodies and Law Enforcement
- Understanding Mandatory Reporting Timelines and Formats
- Liaising with Data Protection Authorities and other Regulators
- Coordinating with Law Enforcement Agencies
- The Importance of Accurate and Complete Disclosures
- Case Study: Simulating a regulatory reporting process for a notifiable data breach.
Module 7: Public Relations and Media Management in a Crisis
- Developing a Crisis Communication Plan
- Crafting Press Releases and Public Statements
- Managing Social Media and Online Reputation
- Preparing for and Conducting Media Interviews
- Case Study: Analyzing the media response to a high-profile cyberattack.
Module 8: Customer and Partner Notifications
- The Art of Delivering Bad News: Transparency and Empathy
- Crafting Clear and Actionable Breach Notifications
- Providing Support and Resources to Affected Individuals
- Managing Inbound Inquiries and Customer Concerns
- Case Study: Role-playing customer notification scenarios.
Module 9: Post-Incident Review and Lessons Learned Reporting
- Conducting a Blameless Post-Mortem
- Identifying Root Causes and Systemic Issues
- Developing a Corrective Action Plan
- Tracking and Reporting on Remediation Efforts
- Case Study: Facilitating a mock post-incident review meeting.
Module 10: Integrating Reporting into the Risk Management Framework
- Using Incident Data to Inform Risk Assessments
- Quantifying the Financial Impact of Incidents
- Communicating Security Risk to the Board of Directors
- Aligning Security Investments with Business Priorities
- Case Study: Building a business case for security improvements based on incident data.
Module 11: The Role of Threat Intelligence in Proactive Reporting
- Leveraging Threat Intelligence to Anticipate and Prepare for Incidents
- Integrating Threat Feeds into Incident Response Workflows
- Reporting on Emerging Threats and Vulnerabilities to Leadership
- The Strategic Value of a Proactive Security Posture
- Case Study: Using threat intelligence to prevent a potential security breach.
Module 12: Reporting Metrics and Key Performance Indicators (KPIs)
- Defining Meaningful Metrics for Incident Response and Reporting
- Tracking Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR)
- Developing Dashboards to Visualize Security Performance
- Demonstrating the Value of the Security Program to Stakeholders
- Case Study: Designing an incident response KPI dashboard.
Module 13: The Future of Incident Response Reporting: Automation and AI
- Leveraging SOAR (Security Orchestration, Automation, and Response) for Reporting
- The Role of Artificial Intelligence in Incident Analysis and Summarization
- The Benefits and Challenges of Automated Reporting
- Preparing for the Next Generation of Incident Response
- Case Study: Exploring the capabilities of a leading SOAR platform.
Module 14: Incident Simulation and Reporting Drill
- Participating in a Realistic Tabletop Exercise
- Responding to a Simulated Security Incident in Real-Time
- Drafting Incident Reports and Communication under Pressure
- Receiving Feedback on Performance from Instructors and Peers
- Case Study: A comprehensive, hands-on incident response simulation.
Module 15: Building a Culture of Security and Continuous Improvement
- The Role of Training and Awareness in Reducing Human Error
- Fostering Collaboration between Security, IT, and Business Units
- Establishing a Feedback Loop for Continuous Improvement
- The CISO as a Business Enabler and Strategic Partner
- Case Study: Developing a security awareness campaign to address common incident causes.
Training Methodology
This course will be delivered through a dynamic and interactive learning experience, combining:
- Expert-Led Instruction: In-depth presentations and discussions led by seasoned cybersecurity and communication professionals.
- Real-World Case Studies: Analysis of high-profile security incidents to extract practical lessons and best practices.
- Hands-On Exercises: Practical workshops on report writing, stakeholder communication planning, and compliance mapping.
- Group Discussions and Peer Learning: Collaborative sessions to share experiences and insights.
- Templates and Tools: Provision of ready-to-use templates for incident reports, communication plans, and compliance checklists.
Register as a group from 3 participants for a Discount
Send us an email: info@datastatresearch.org or call +254724527104
Certification
Upon successful completion of this training, participants will be issued with a globally- recognized certificate.
Tailor-Made Course
We also offer tailor-made courses based on your needs.
Key Notes
a. The participant must be conversant with English.
b. Upon completion of training the participant will be issued with an Authorized Training Certificate
c. Course duration is flexible and the contents can be modified to fit any number of days.
d. The course fee includes facilitation training materials, 2 coffee breaks, buffet lunch and A Certificate upon successful completion of Training.
e. One-year post-training support Consultation and Coaching provided after the course.
f. Payment should be done at least a week before commence of the training, to DATASTAT CONSULTANCY LTD account, as indicated in the invoice so as to enable us prepare better for you.